We hate to upset you, but things are pretty sad when it comes to the security of phone calls and messages these days.
According to the statistics of our test lab, in 95% of cases, our expert needs only several hours to find a relatively simple way to hack a device that is used for your important calls and text messages.
In general, the heart of the matter is that practically none of the modern communication devices were originally made to be safe.
All these devices were made to serve specific purposes and functions, and security is initially beyond their scope.
Attempts to add “protection” or “cryptography” to an insecure solution look like hanging a high-quality lock on a cardboard door.
Or like installing a security door onto a shabby fence:
Actually, an ordinary person wouldn’t be bothered in this situation – “Come on, who’s interested in my phone calls?!” – majority of people would say, and they would be right.
However, when there is a need to protect important business conversations, prevent a leakage of commercial secrets, or guarantee confidentiality of your clients when they are communicating with you, whether you want it or not you start asking yourself: “Is it actually possible to find solutions that guarantee secure communication?”
To make things clear, let’s first see what’s wrong with the generally known and widely used means of communication.
- Mobile Telephones and SMS
Theoretically, there is a SIM card which is actually a smart card, and a phone, which initially uses some encryption (that has never been publicly checked).
But what does it looks like in practice?
All this wizardry in one way or another is actually based on the old (by old we really mean it – 1970) SS7 protocol. This protocol is widely known as a vulnerable one, and more than that, the solutions with the source code of how to exploit these vulnerabilities are publicly available.
And it is actually impossible to fix the situation – all this stuff is hardware-programmed and costs hundreds of millions of dollars, in addition, the mobile operators themselves are not interested in protecting phone calls from interception.
So it’s not surprising at all that every once in a while the press publishes scandalous records of the private conversations of famous politicians and celebrities.
- Ordinary “landline” communication
The same transparency for intelligence agencies and total lack of any encryption. Meaning that one needs only basic knowledge in radiotechnics to intercept someone’s conversation.
- Mobile phone (smartphone) + some (any) communication app
In a majority of cases we talk about Android and Apple.
Android
Everyone knows it’s leaky. This is the reason why every month new rootkits, viruses, Trojans appear and easily penetrate the phone without user’s awareness.
Here’s the statistics of the past years:
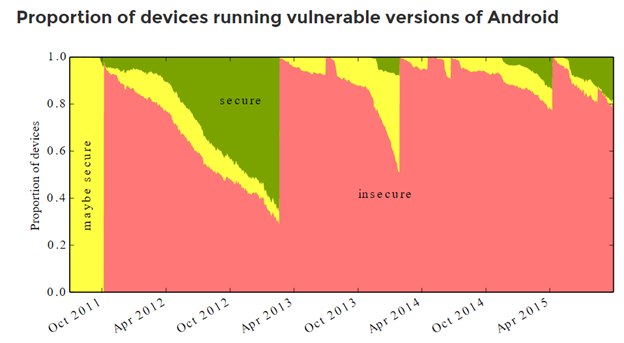
And here are a couple of this year examples:
275 million Android phones imperiled by new code-execution exploit
Unpatched “Stagefright” vulnerability gives attackers a road map to hijack phones.
DAN GOODIN – 3/18/2016, 10:26 PM
QuadRooter: New Android Vulnerabilities in Over 900 Million Devices
by Adam Donenfeld, Check Point Mobile Research Team posted 2016/08/07
http://blog.checkpoint.com/2016/08/07/quadrooter/
By the way, because of the variety of phone producers (every one of which adds its own holes into the operating system) one can hardly imagine what can be done here at all.
Something could be done by Google. But guys at Google seem not bothered.
Applе
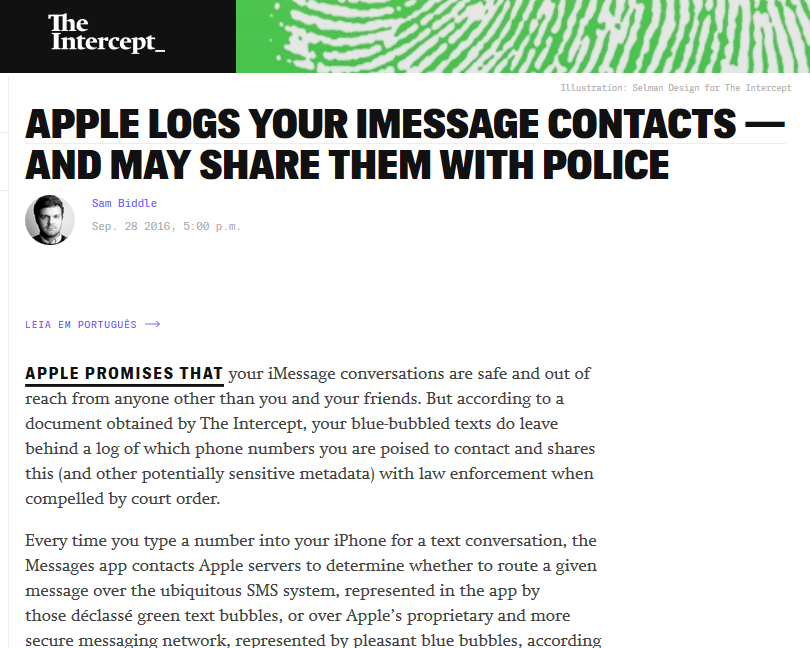
Apple seems to be making some efforts to improve the system security. But all in vain. iPhone 7 was hacked within 24 hours after its release.
By the way, let’s make sure everyone understands the actual reasons of the recent conflict between the FBI and Apple: the problem was about legal issues only. That was the case when intelligence agencies tried to make a producer provide a standard set of solutions to crack its own system.
Practically, it’s not a problem for police to hack an Apple device (which was eventually done). The thing was how to do it without bothering with sanctions on using special means.
Microsoft – It’s just sad, google it, or what…
Other rare systems
Unfortunately, they are built on the same basis. For instance, Blackberry uses Android elements for compatibility with Android apps, with all the security consequences that come with it.
And how are things with popular messengers and calling software?
In fact, there are quite a few ways to hack them, so we will mention briefly only the most obvious ones.
Skype
It’s been a long time since Skype used to be peer-2-peer. Now, everything is passing through the Microsoft servers. Which, of course, will share any information with those who require it.
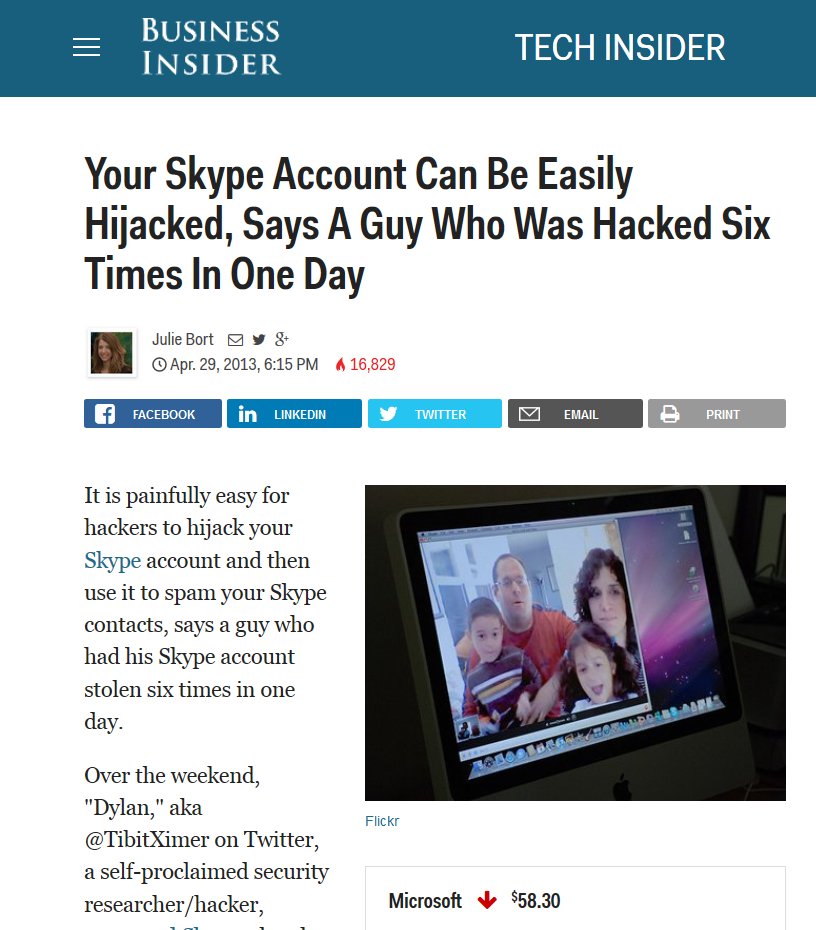
And the application itself is not so stable (you’ve noticed, if you use it, haven’t you?) In addition, it supports the unchecked plug-ins. All it takes is just a 3rd party plug-in to record everything that’s needed.
WhatsApp, FB Messenger
(It makes sense to consider them together, because these messengers share data with one another and eventually are going to unite into a single system).
One should mention that WhatsApp has a really good cryptography – there’s nothing to complain. But the question is, who keeps the keys and controls the access to the account?
And once again, the solution wasn’t initially made as a secure one – instead of message interception, it’s easier to hack an account and receive access to conversations (or start writing on the user’s behalf). Account protection is attached to SMS by default, and SMS is an ancient SS7 protocol, which we’ve mentioned earlier.
As for FB Messenger, it is susceptible to all those viruses that are on Facebook right now. Because FB Messenger is integrated with the FB-platform, and it is hacked more than regularly, as you’ve probably noticed.
Telegram
This is an example of a “secure” messenger which actually is not. Features along the line of “disappearing messages” are good, but security is not a word for it.
Cryptography, in contrast to WhatsApp, is of uncertain origin and checked by no one.
And one can hack the account just the same way as with WhatsApp – again SMS and again SS7 protocol.
There is no protection from viruses and other interference into Telegram app. More than that, there are specific paid apps which wiretap Telegram.
By the way, other messengers can be wiretapped as well.
If you are interested, here’s a short list of what can be “listened in” by such a software:
- Facebook, Facebook Messenger
- Viber
- Skype
- Line
- iMessage
- BBM, Blackberry PIN
- Telegram
- Yahoo Messenger
- Snapchat
- Hangouts
- KIK
- Tinder
And it is a matter of several hundreds of dollars only.
But even with quite secure solutions which are not controlled and/or checked regularly by the specialists, you will have serious security problems.
A good example is a secure network Tor, which is very good in terms of security: open source code, etc.
But what a nuisance – the node network, through which a protected traffic goes, was poorly controlled. As a result, more than 100 servers were accidentally (!) disclosed – they passed the traffic of the network users and wiretapped it:
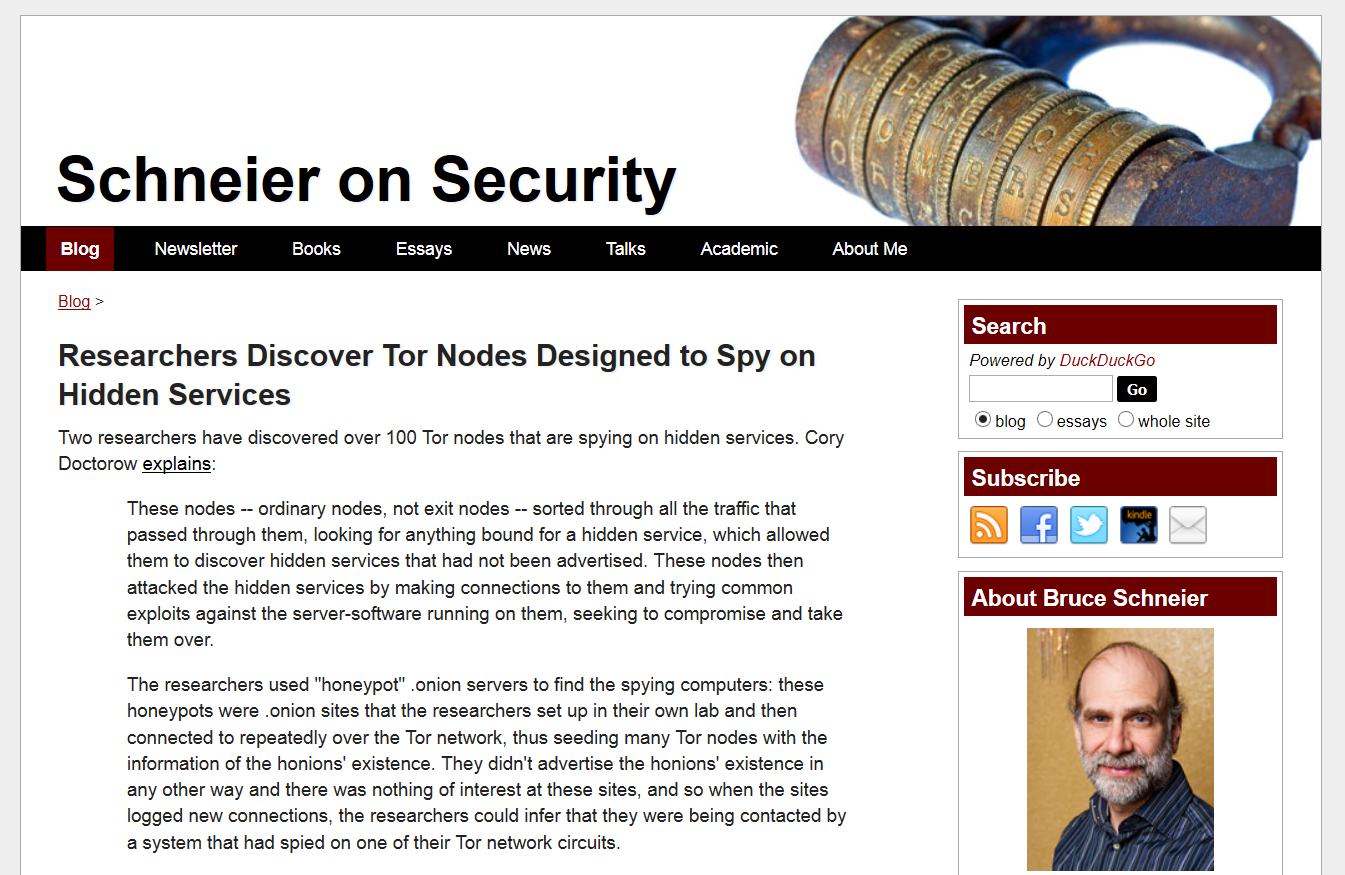
So Tor, being a great idea of the enthusiasts, turns out to be even more harmful for those who need anonymity, since they all are gathered together and easily tracked – no need to bother with call interception or spying program installation.
So what is to be done? Is it impossible indeed to protect our conversations and text messages?
Actually, this situation is entirely preventable.
But for a start, one should understand the main principle:
A solution can be secure only if it is fully under your control.
Let’s decipher what “full control” means, and how to reach it with a help of our solution.
The Phone with a safe OS
It’s a bit naïve to try to protect your conversations and at the same time keep using a smartphone with a standard OS.
That is why we’ve developed our own operating system, which fully eliminates the risk of penetration through apps, social networks, etc.
Naturally, such OS should be set on a specially “prepared” smartphone.
As a result, we have created a safe smartphone – SV Phone, which cannot possibly be attacked by viruses, Trojans, and other standard hacking means.
Our SV Phone looks like an ordinary smartphone
There are several models of so-called cryptophones on the market. However, all of them have a crucial deficiency – if seen in your hands, this phone shows that you certainly have something to conceal. More than that, mobile operators immediately detect that you use specific equipment.
It’s like hanging a sign on your chest that says, “Hey, look at me, I’m hiding some information!”
Our SV Phone is based on a standard model of Nexus and is very similar to an ordinary phone.

What is more, during the conversation your mobile operator won’t be able to track even the fact of the conversation itself – it will look like an ordinary VPN-connection (as if you connected to the Internet).
How about the level of encryption?
Now, let’s focus on the protection from wiretapping and message interception.
The thing is that our main business is development of complex encryption systems for protection of conversations and messages for governmental institutions and corporate giants. Thus, we are just obliged to have a governmental level of cryptography (otherwise we couldn’t be in the business).
That is why we have an possibility to use the highest possible level of cryptography even for a retail software.
Even if you are not an expert in cryptography, look at the table below:
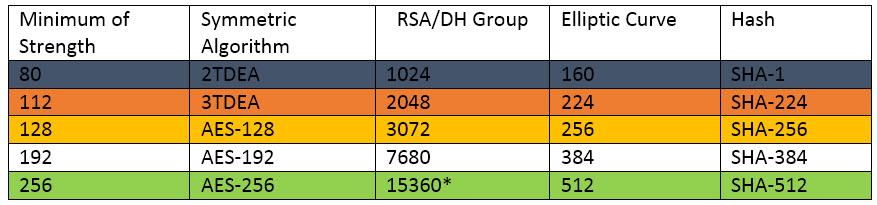
To be on the highest level (AES 256), all the parameters must be on the same level of security as the system in general.
If even one parameter in the black line bl is lower, the system is very easy to hack. The parameters of the orange line or correspond to the high-risk level, yellow ye – lower risk, but one should remember that security will be AES-128, and not 256. The white line is recognized as quite safe. And the green one gr means the highest “TOP SECRET” security.
In our solution, all crypto-parameters fully comply with the green line in the table.
Personal server guarantees the full control over your conversations
Now, let’s move to the key element of the security system.
All existing cryptophones, apart from attracting additional attention to you, have one serious drawback. The connection is made through the servers of the companies that sell these solutions.
So if special services need to receive some information about your conversations, they have a right to address the provider.
In our case, there is no provider at all. You just buy an ordinary server, deploy our system (we’ll help you with that), and from now on, your connection goes through it only (once again, it won’t even look like you are making phone calls).
How to start using our system “SV Phone + personal server”?
Step 1. It’s better to start from purchasing two SV Phones – this will let you start using a secure connection, even if you don’t need to add many users to it yet (in this case, you will have the protected channel between two purchased SV Phones). The price of one SV Phone is 650 Euro.
Step 2. For the highest level of confidentiality it is better to connect through your personal server. The price of our server license is 9 900 Euro. Within two workdays we deploy our solution on your server. Server license includes additional 10 licenses for your mobile devices (we install an app on your smartphones, that will allow to make connections through your server).
If you need to connect more devices, you can buy additional SV Phones or additional licenses for your mobile devices without change of initial server license price.
Should you have some questions, or if you want to make an order, please, leave your contact info and we’ll get in touch with you within one workday.
You can request a free security advice here: