The minimum level of security is always important. Normally it is scored as an equivalent of the symmetric encryption bits.
And it is not equal to the bits your algorithms are using. It is the least secure point in your solution.
It is а standard that voice is encrypted with AES 256. Unless the special attack is used (see below) the attacker will not attack it. Attacker first will try to get the key. One way is to get it during the key exchange.
Here is the table with minimum level of security depends on the key exchange algorithms used. We have taken it from the NIST Recommendations.
At our solution we implement ECC 571 and/or DH 16 384* key exchange which is even above the requirements. *Some customers ask to implement DH 8192 because of the certification reasons.
9+ layers of security
Multiple locks are normally better than one, especially if you can loose the key. Our system is designed for virtually unlimited multi layer implementation. So number of layers can be changed per request. In the fully implemented platform there are 9 (!) layers of security:
- 3 key exchange channels (either independent or 2 of them can have completely different algorithms and 3rd is a mix from 2 channels)
- 3 cascade symmetric encryption
- 1 HSM module authentication (if device have SD slot for SD-HSM)
- 1 device watermark authentication
- 2 additional “can be modified by customer” algorithms
Some of these layers could be implemented by the customer if required by the project.
Works on modern mobiles
SV works on all modern iOS and Android devices from the box. Other platforms are added easily on request.
Standard platforms:
- iOS 9.x, 8.x, 7.x
- Android 6.x, Android 5.1.x, 5.x, 4.4 @ .x, 4.3.x, 4.2.x
- SV Deskphone
Desk-phone version is available

You can have SecureVoice IP Deskphone staying on your table fully compatible with mobile software.
More platforms on request
SV designed with multi platform approach in mind. As a results platforms can be introduced fast by adding platform specific UI/UX.
Here are platform list where SV core already works:
- Windows 10, 8.x, 7
- Mac OS
- Linux
- Blackberry 10
- Windows Phone 8.x
Management Panel
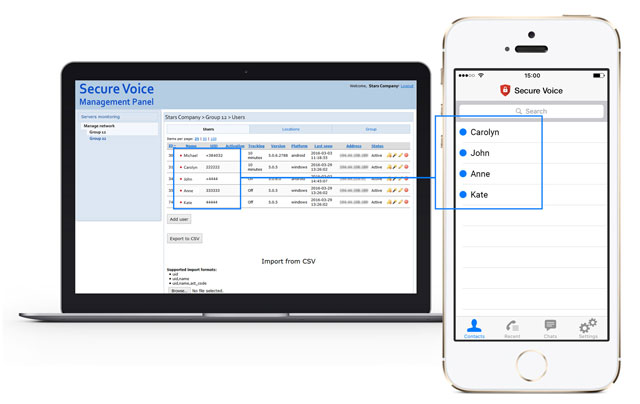
Management of customers, groups, users and configuration settings
World top class audio engine
Meet the results of 9+ years of selection and competition between audio engines.
In the result is works best in both mobile worlds: one with LTE, 3G and the one with older networks.
Codecs are dynamically changing and you will have HD sound with the high bandwidth on LTE, while software will automatically reduce the usage in the 2G networks up to the tiny 4.75Kbit codec.
Works good in both modern and old mobile networks
Years of trials in more than 50 countries result in the software that are quite tolerate to the changing network condition.
As a result software is working in 4G, 3.5G, 3G, 2.75G, 2.5G and 2G networks
Here are the list of networks we have optimized it for:
- LTE, TD-LTE, LTE Advanced
- IEEE 802.11 (WiFi): 802.11b, 802.11b/g, 802.11n
- HSDPA+, HSDPA
- UMTS, UMTS-TDD
- HSPA, HSPA+
- CDMA EV-DO (Rel. 0, Rev.A, Rev.B)
- EDGE, Evolved EDGE
Permissions to call and see who is online
Assigned administrator can divide persons in groups and arrange who is able to see/dial/chat with each other. In this way you can isolate e.g. top members from regular staff, while still allow e.g. department head to connect to the head of the division.
Closed Group usage (Corporate Address Book)
Secure Voice support closed groups. For the closed group of people or agency it make sense that no one else can dial in. This can be done either permission based or even for highest level of confidence by modifying encryption algorithms especially for the particular agency.
Encrypted voice calls, point-to-point
Governmental encrypted calls in one click. The encrypted voice are sent from device to device in the shortest route possible.
New ephemeral keys for each voice call
For each call new random ephemeral keys are generated and destroyed after the call.
For longer calls there is an customization option to change ephemeral keys during the call.
Encrypted Instant Messaging
Instant Messaging with full governmental encryption and fast message propagation.
Users are divided in groups.
Encrypted Group Chats for 500 users in one chat
Governmental encryption for up to 500 users right from the box.
In the available customized version this can be extended to 1000 or more.
Encrypted Push-to-Talk for Large Groups
You can have hundreds of people listening on the channel to the command.
Encrypted File Transfer
Files are transmitted point-to-point encrypted with the same governmental security level.
Works in completely isolated network
Secure Voice is designed to work in isolated environment.
Some tested examples:
- Corporate Intranet
- On a ship
- In the desert
- MPLS network
- VPN
Works internationally and in multi-country set up
SV works internationally from the box. You can install SV server in your country and go thousands kilometers away and still would have a good conversation quality.
Additionally there is a way to have shortest possible time for countries interconnect even if direct traffic between phones are blocked.
SV regional servers can be deployed to support large aboard units
Can work without Push for the maximum security
Most software on the market will use Apple’s or Google’s push messages. This theoretically have no impact on the security, but practically gives out some (even very small) info about the call made between devices.
SV can be configured to work without using any 3rd party push services to save every single bit of security.
Can work with Push to extend battery life
If you use standard software on your devices than Push is already in use.
In this way it may be reasonable to enable Push usage to extend battery life.
Coming soon
Secure Voice is constantly evolving. And you can be driver as soon as you submit the request.
However here are short list from our timeline. These features are already “tested in lab”.
Means you can have them fast if needed
- Encrypted Conference Calls
- Encrypted Video Calls
- Secure Double Telepresence Robot
- NFC as additional authentication factor
Absolutely No Backdoor
The Secure Voice is made with absolutely no backdoor and comes with a number of possibility to checks this.
Just a few basic points:
- As a customer you can come for the complete source code review
- As a customer you can “build your own server” from the source code
- In deeply customized version you can own the source code (on the non exclusive bases of course)
- You can (and our customers always do) perform all blackbox testing of the software
- You always can have own server at your own premises
- The software can be 100% isolated from Internet and public networks if needed
………………
Interested? Next step: get free advice from our encrypted communication expert.
In order for you to choose which method is appropriate for you to protect your phone conversations and SMS we offer free security advice.
Choosing the right solution depends on many parameters:
- which channels of communication are being used
- how many offices will be using such a system
- number of users of the encryption network
In some situations a complex multi leveled system has to be used in others a simple solution is sufficient.
We will let you know what type of protection suits you best based on our experience.
You can request a free security advice here:
Contact us using the contacts bellow:
Tel: +49 335 2288 3873
Skype: fivepro.customer.care
Monday-Friday 10:00 – 18:00 CET
Email:
info@secure-voice.com